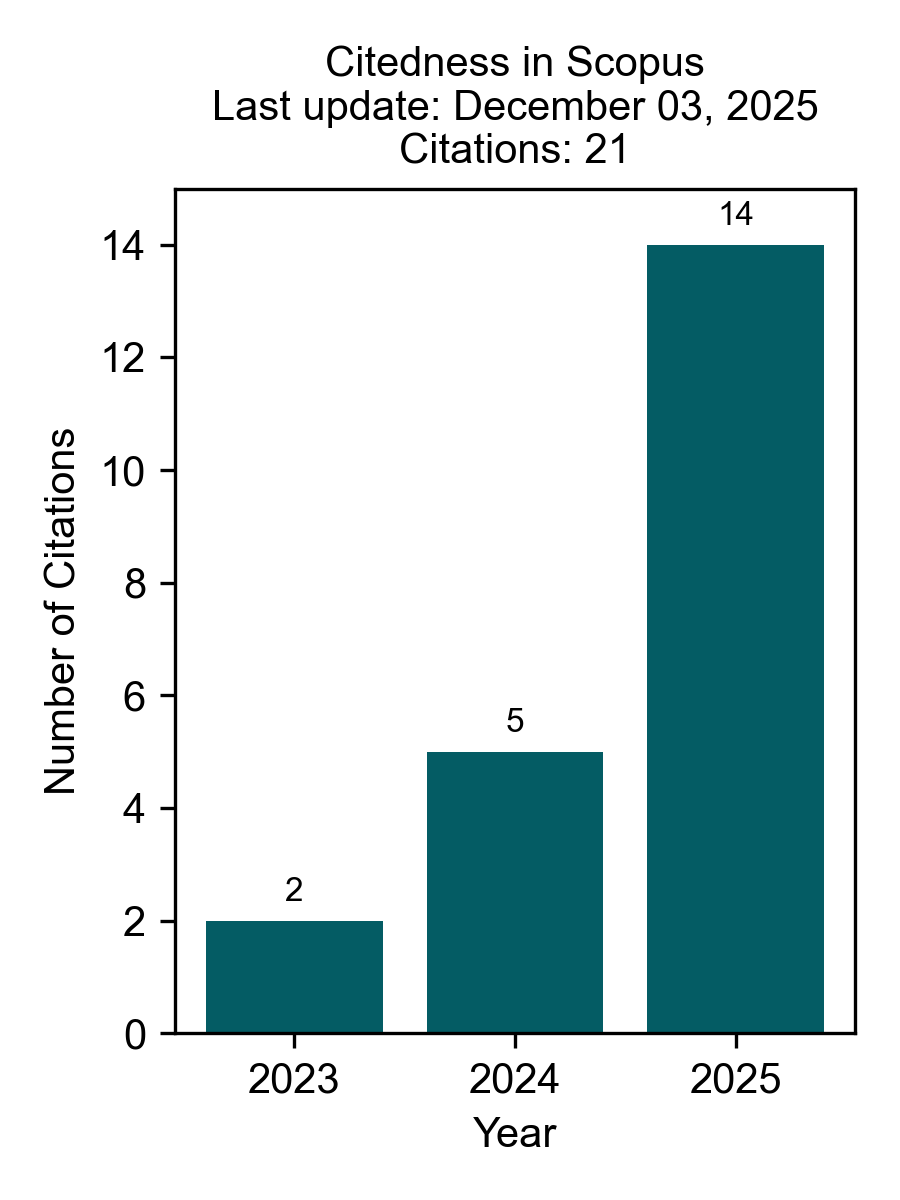|
TEMPLATE |
Citedness in Scopus
Citedness of Journal Articles in Scopus.
 |
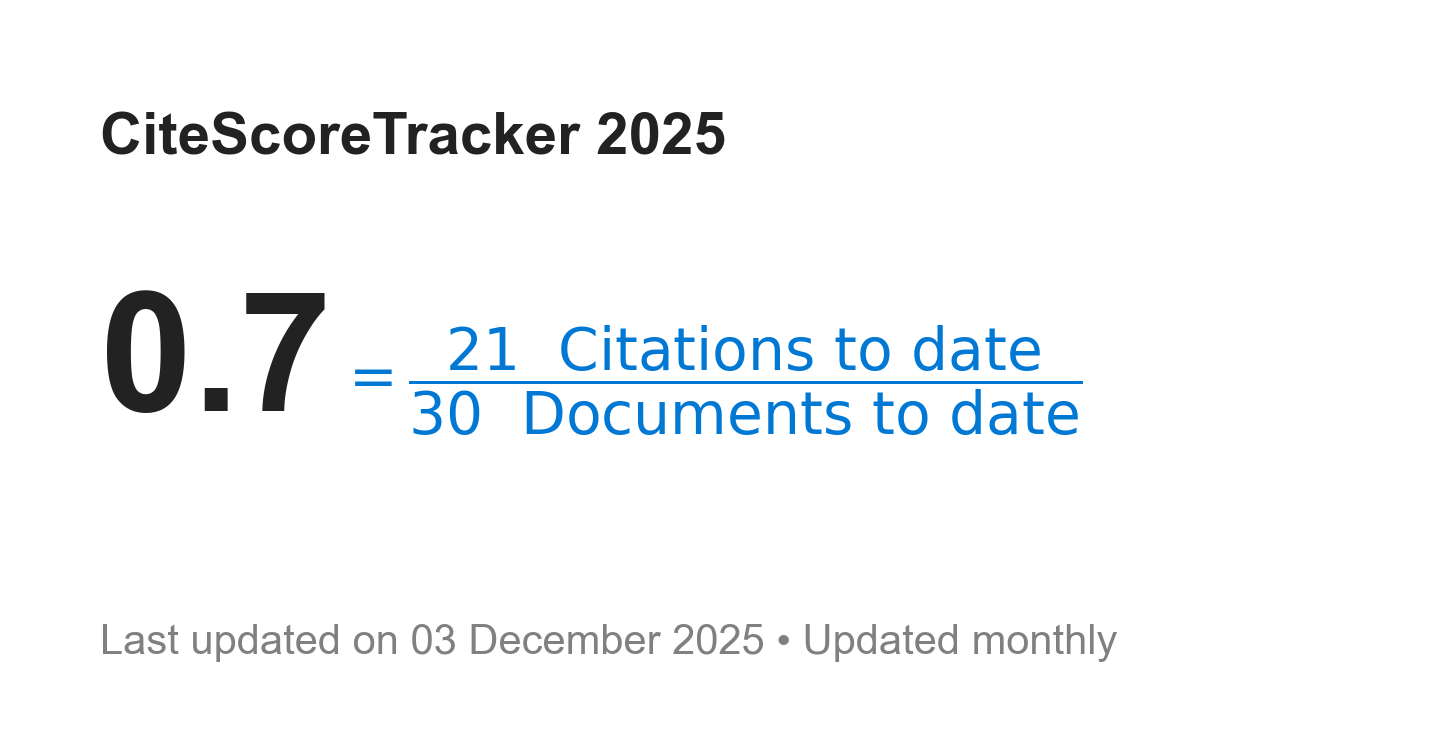 |
Journal of Information Technology and Cyber Security (JITCS): Number of cited documents: 43% (13 out of 30 articles); cited by 21 documents indexed in Scopus. Updated on December 03, 2025.
-
Journal of Information Technology and Cyber Security: 10 documents, 17 citations.
-
J Inf Technol Cyber Secur: 2 documents, 2 citations.
-
J Inform Technol Cyber Secur: 1 document, 1 citation.
-
Recommendation System Using the K Nearest Neighbor Approach A Case Study of Dual Camera Quality as A Smartphone Selection Criterion: 1 document, 1 citation.